Next Steps
As a next step, we will look at the stateful confidential program. This consists of five different confidential applications:
- a confidential
memcachedused as a rate limiter, - a confidential
nginxas a TLS terminator, - a secure document service that implements the business logic,
- a confidential MariaDB instance to store the state, and
- a confidential client to send requests.
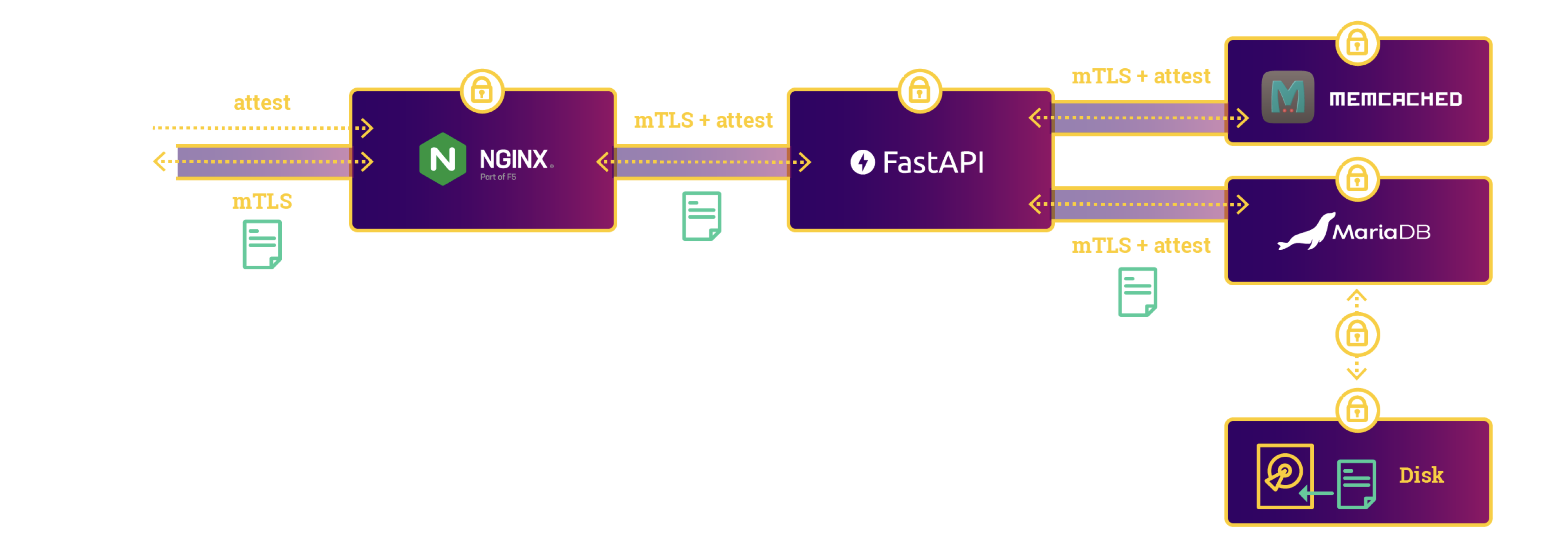
Please have a look at SecureDocumentApp for more details.