Deploying with kubectl
In this section, we describe how to deploy confidential services with kubectl instead of helm.
Prerequisite
We assume that you already read Section Sconifying A Stateful Service.
Deploying confidential containers with kubectl
helm version 2 had some disadvantages. helm version 3 has improved quite nicely, e.g., it does not need
to run services in you Kubernetes cluster anymore. Still, not everybody wants to use helm to deploy confidential containers.
In this case, one can use kubectl to deploy confidential container images. The workflow is as follows:
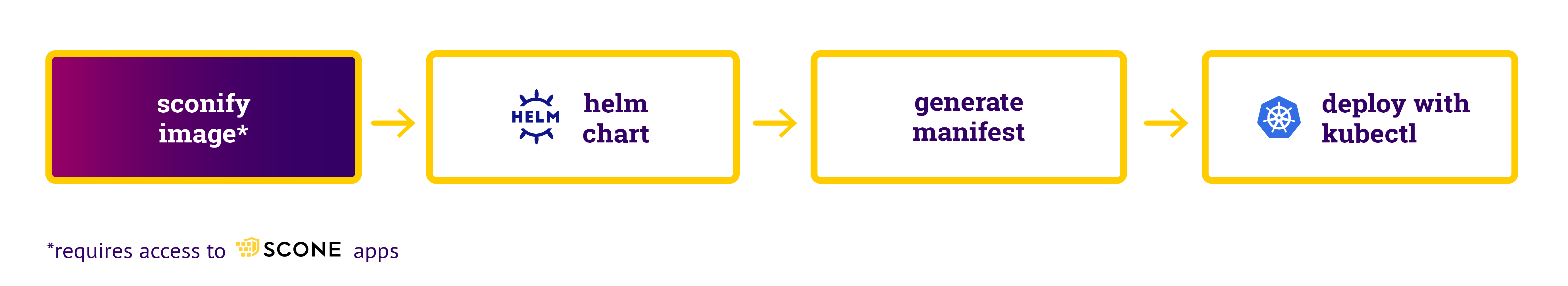
We use sconify_image to generate a helm chart. We translate this helm chart into a manifest. We can deploy the manifest with the help of
kubectl.
Example
For the hello world example, we can generate the manifest as follows:
helm template python-service charts/python-service > manifests.yamlNow you can deploy this manifest with the help of kubectl:
kubectl create -f manifests.yamlYou can of course modify the manifest. The manifest might look as follows:
---
# Source: sconify-python-service/templates/job.yaml
apiVersion: batch/v1
kind: Job
metadata:
name: python-service-sconify-python-service
labels:
helm.sh/chart: sconify-python-service-0.1.0
app.kubernetes.io/name: sconify-python-service
app.kubernetes.io/instance: RELEASE-NAME
app.kubernetes.io/managed-by: Helm
spec:
template:
metadata:
labels:
app.kubernetes.io/name: sconify-python-service
app.kubernetes.io/instance: python-service
spec:
restartPolicy: "Never"
volumes:
- name: volumev1
emptyDir: {}
containers:
- name: sconify-python-service
image: "registry.scontain.com/christof.fetzer/hw-k8s:python-k8-test-22166"
imagePullPolicy: Always
securityContext:
capabilities:
add: ["SYS_RAWIO"]
env:
- name: SCONE_CONFIG_ID
value: ns-20726744429579/python-session/python-service
- name: SCONE_CAS_ADDR
value: 5-3-0.scone-cas.cf
- name: SCONE_LAS_ADDR
valueFrom:
fieldRef:
fieldPath: status.hostIP
- name: SCONE_ALLOW_DLOPEN
value: "1"
- name: SCONE_HEAP
value: 256m
- name: SCONE_STACK
value: 4m
- name: SCONE_LOG
value: "ERROR"
resources:
limits:
sgx.intel.com/enclave: 1
volumeMounts:
- name: volumev1
mountPath: /V1
initContainers:
- name: check-attestation
image: registry.scontain.com/clenimar/attestation-check:latest
imagePullPolicy: IfNotPresent
env:
- name: SCONE_CAS_ADDR
value: 5-3-0.scone-cas.cf
- name: SCONE_LAS_ADDR
valueFrom:
fieldRef:
fieldPath: status.hostIPNext Release
In the next release, we plan to add an option to sconfiy_image to be able to generate a manifest directly. This will reduce the need to install helm on the development machine.
