Secure Remote Execution
We show how to execute applications in an always encrypted fashion on a remote, untrusted machine via a simple CLI (Command Line Interface). The CLI runs inside a container on a trusted client computer:

Prerequisites
Remote host installation
You need to install the SGX driver and Docker engine.
So far, we support the execution on remote hosts / VMs via ssh and via the iExec platform. To start a container on a remote host via this CLI, you need to give the CLI the credentials of this hosts. These credentials are stored in a volume stored on the client's computer. In this example, we use directory $PWD/conf/ to store the credentials. Ensure that only you have access to this directory to protect the credentials. This directory must be mapped in the container at location /conf:
eval docker run -it --rm -v $PWD/conf/:/conf registry.scontain.com/sconecuratedimages/iexecsgx:cli add-host --alias caroline --hostname 1.2.3.4This adds an alias (caroline) for the host identified by option --hostname. The argument --hostname can either be a hostname or an IP address. The CLI generates a key pair inside the container and stores it in /conf. The public key is used to grant access to the container on the remote host.
The output of add-host will look something like this:
ssh ubuntu@1.2.3.4 "echo \"ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDXVqr0diJjgMPx7WNTQWJVhV3ea8L1I/8mDZTsQUH5gazB+laIiM7tEAKbddbessItmA9bLOZEq4CIrYmtXpjG2tBSES2YpqNhQ8+3r4U3ozSBD1XAc6OzRmnHP+wmuVpCQw0QxBKj0Qq5MCehmLIXLYephOtjVWwsA3EprVHIq0+/wYZp4mU3evCgcvE46nxOrmHzu5X4iDUMSY59XHdavIVkkS87qp4RlyFQa0gBRHOfcGEVJ3oS/pmKHxasdLwjiVmCovLG4RPS88RoKCf8zWis8vpPUKt/04xjlj4gqsV/U7VR2S/kFcvq1yuvOno+BhcsGme2U2CKTV4Y16ZJ scone-CLI\" >> .ssh/authorized_keys"eval executes the output and gives your local client to give the container access to the remote host.

Execution
To execute an application on a remote host, you first have to add this host via add-host as described above. We show how to execute the simple copy application that we introduce in the next section of this tutorial. This copy application takes some input files in a given directory INPUTS and copies these files to directory OUTPUTS in a very elaborate way:
- encrypt the files in directory INPUTS inside the container running on the client machine
- push the encrypted files to a remote file service - which is operated by an entity that we do not know
- start the copy application container on a remote host - which is given via option --host HOST
- a script running inside the container pulls the encrypted files from the remote file service
- the script starts the copy application inside of an enclave
- the SCONE runtime transparently decrypts the input files and transparently encrypts the output files
- the SCONE runtime ensures both the confidentiality as well as the integrity of the files
- the copy applications copies the input files to the output files and then terminates
- the shell script pushes the encrypted output files to the remote file service
- the CLI pulls the output files from the remote file service and decrypts the files and stores the files inside the OUTPUT directory.
The copy application is stored in image registry.scontain.com/sconecuratedimages/iexecsgx:copy_demo on registry.scontain.com. You can execute this image as follows:
docker run -it --rm -v $PWD/INPUTS:/inputs -v $PWD/OUTPUTS:/decryptedOutputs -v $PWD/conf/:/conf registry.scontain.com/sconecuratedimages/iexecsgx:cli execute --application sconecuratedimages/iexecsgx:copy_demo --host carolineExample: Copy Demo
You could perform the following steps to see the copy_demo in action. Create some directory and a file to copy.
mkdir -p INPUTS OUTPUTS
echo "Hello World" > INPUTS/f1.txtNow execute the copy application (as shown above):
docker run -it --rm -v $PWD/INPUTS:/inputs -v $PWD/OUTPUTS:/decryptedOutputs -v $PWD/conf/:/conf registry.scontain.com/sconecuratedimages/iexecsgx:cli execute --application sconecuratedimages/iexecsgx:copy_demo --host carolineThe file f1.txt was copied to directory OUTPUTS. You can check the output, by executing:
cat OUTPUTS/f1.txtwhich results in the output:
Hello World
Example: Blender
We show to run blender with a blender file. To do so, show to render some blender file from our collaborator iExec as well as some other blender files accessible via github.
Setup
Let's set up an EXAMPLE directory and create some sub-directories for input and output files. We also need to specify
- a remote file service like transfer.sh or filepush.co/upload, and
- an instance of the SCONE CAS configuration and attestation service.
mkdir -p EXAMPLE
TRANSFER="transfer.sh"
CAS=scone-cas.cf
cd EXAMPLE
mkdir -p conf INPUTS OUTPUTSTo reduce the typing, let's define an alias for the secure remote execution of blender:
alias aeblender="docker run -it --rm -v $PWD/INPUTS:/inputs -v $PWD/OUTPUTS:/decryptedOutputs -v $PWD/conf/:/conf registry.scontain.com/sconecuratedimages/iexecsgx:cli execute --application sconecuratedimages/iexecsgx:blender --host caroline -r $TRANSFER -s $CAS"We assume that you added the host (in this case caroline) already via add-host (see above).
Render Image
Let's first download a blender file:
curl https://raw.githubusercontent.com/iExecBlockchainComputing/iexec-dapps-registry/master/iExecBlockchainComputing/Blender/iexec-rlc.blend -o INPUTS/iexec-rlc.blendand we render this blender file remotely ensuring all artifacts are always encrypted:
aeblenderWe can now look at the files in OUTPUT directory:
open OUTPUTS/0001.pngWhich shows the following picture which was computed using always encrypted approach:

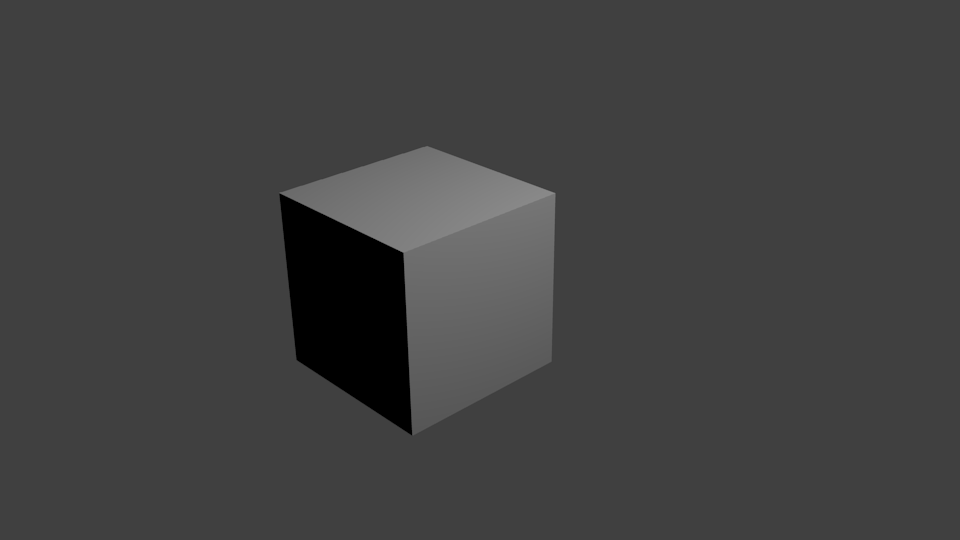
Cube
Let's download another blender file from github:
curl --output INPUTS/iexec-rlc.blend https://raw.githubusercontent.com/golemfactory/golem/develop/apps/blender/benchmark/test_task/cube.blendand render this blender file on the remote and untrusted host caroline:
aeblenderThe OUTPUT directory contains the following picture - which was computed remotely with all data and processing being always encrypted:
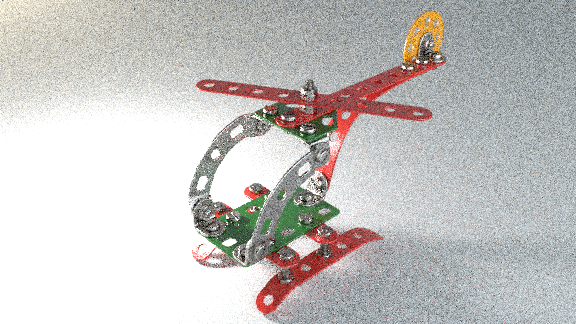
Helicopter Example
Another example from github:
curl --output INPUTS/iexec-rlc.blend https://raw.githubusercontent.com/golemfactory/golem/develop/apps/blender/benchmark/test_task/scene-Helicopter-27-cycles.blendWe are execution with the same command as above:
aeblenderThe OUTPUT directory contains the following picture - which was computed remotely with all data and processing being always encrypted:
Car Example
We show one more example:
curl --output INPUTS/iexec-rlc.blend https://raw.githubusercontent.com/golemfactory/golem/develop/apps/blender/benchmark/test_task/bmw27_cpu.blendand render this (as above):
aeblenderThe OUTPUT directory contains the following picture - which was computed remotely with all data and processing being always encrypted:

Advanced Example
You can also run blender with Python scripts that describe your images and movies - see blender use case for details.