SCONE Confidential Code Deployment
We have witnessed in several contexts the following problem: Multiple stakeholders want to collaborate in some joint project. However, they have limited trust in each other since they are also competitors in different projects. Since some money might be at stake, some stakeholders might not play by the rules to get some advantage over the other stakeholders.
For example, the stakeholders might want to pool their data to provide a joint service. They want to use the data to build models using federated machine learning. A stakeholder might not want to provide all its data to the other stakeholders to get some competitive advantage (a freeloader). Or, it might give access to corrupted data only (a Byzantine stakeholder). The stakeholders might want to ensure that
- all participants can use the same training data, and
- participants can only access their training data in the clear.
To solve this problem, the stakeholders could agree on a joint codebase:
- they agree that they use a joint, agreed-upon codebase. This codebase is hosted in some git repo,
- each participant has access to the git repo and can inspect the code, and
- the code will need to be updated periodically.
All stakeholders need to agree on the code base. To do so, one can use the SCONE CAS policy board to agree on a common policy:
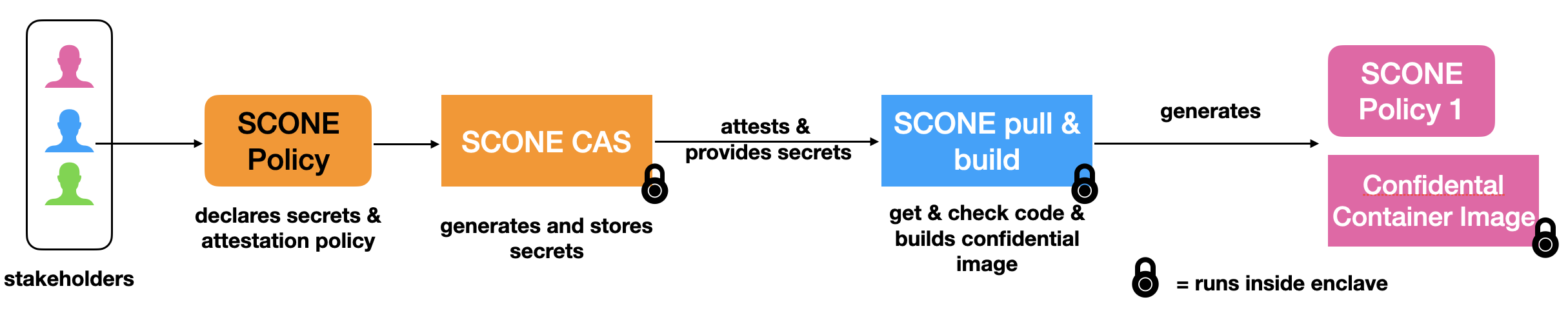
This policy permits each stakeholder to create a confidential image of the source code using a confidential application that pulls the code and creates a confidential container image which runs the agreed codebase, i.e., a confidential service. The stakeholders can deploy the confidential services and also the policy in clouds or datacenters of their choice.
The confidential services can attest each other automatically via TLS. This is the case even if the policies of the individual confidential services would use different CAS instances to store the policies.
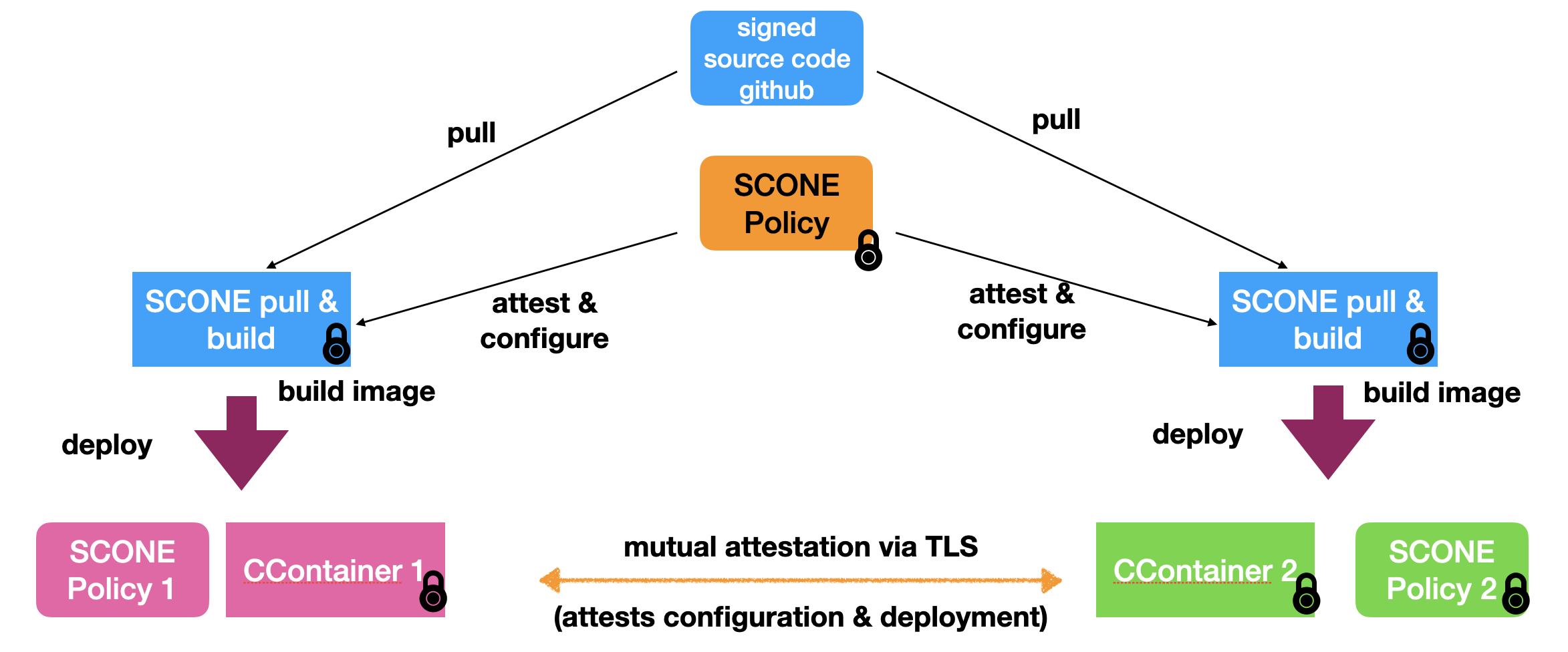
For more details on how to set this up, please send us an email.