Confidential Computing with SCONE
Deprecation warning
All SCONE versions prior to 6.0.0 will be deprecated with the sunsetting of the DCAP v3 Intel PCS API on October 31st 2025 the latest! It is mandatory to upgrade CAS and LAS to 6.0.0 before October 31st 2025 to ensure continued operations. SCONE 6.0.0 is set for release within the next few weeks.
Scone Version 6.0 is now available (2025-08-08)
SCONE 6.0 is released adding support for Intel DCAP v4.
Scone Version 5.10 is now available (2025-07-02)
SCONE 5.10 is released. It contains numerous new features, many bug fixes, and improvements in CAS and runtime.
Scone Version 5.9 is now available (2024-08-07)
SCONE 5.9 is released. It contains numerous new features like WAL (Write-ahead logging), many bug fixes, and improvements in CAS and runtime.
Register at our container registry to get access to our community edition
You can register a free account at https://gitlab.scontain.com to get access to our community edition. For more details, please have a look at our Scontain Registry documentation. To evaluate sconify_image, please contact us via email.
Updated Secure Arguments and Environment Variables tutorial (2024-1-15)
The updated Secure Arguments and Environment Variables tutorial shows how to create a simple confidential application, create and update policies to pass arguments and environment variables to this program, and execute confidential applications in production mode.
Description of SCONE policy language 0.3.11 (2023-8-25)
A new version of our policy language aka SCONE Session Language 0.3.11 is released. We added a variety of new policy features like policy fragments and governance.
Scone Version 5.8 is now available (2023-6-19)
SCONE 5.8 is released. It contains a large number of new features like governance and air-gapped operations.
The SCONE Operator is now available (2022-12-12)
The SCONE Operator supports the deployment, reconciliation, and update of the SCONE SGXPlugin, LAS, and CAS. We also support a kubectl plugin to provision the CAS for production mode.
Air-Gapped Operations with Platform-Based Attestation (2022-11-19)
SCONE supports air-gapped operations. For example, we can protect applications running in an environment in which the application owner does not have access to attestation services. We added a simple example for platform-based attestation.
A convenient way to configure native applications (2022-10-28)
We support the configuration of native applications with the help of SCONE CAS: command envcas permits to set the arguments, environment variables, and configuration variables. One can even require an OTP to be able to start the native application. One could for example use this to configure native applications with certificates and public/private key pairs.
Simplified approach and new tutorials (2022-09-09)
We have a new way to build confidential applications. We have added a new QuickStart that helps to set up all prerequisites and to build the first confidential Python program.
Confidential Document Management Application (2022-02-04)
We released an updated Confidential Document Management application. All services running inside of enclaves:
nginx-based gateway, FastAPI-based business logic, memcached-based rate-limiter, and MariaDB-based document store. The services are connected via mTLS, i.e., perform implicit mutual attestation. All data at rest is encrypted. A client can attest the application via mTLS. We added a new screencast introducing this application.
Released SCONE Version 5.7 (2022-01-26)
We released SCONE version 5.7. This includes a set of stability improvements and a large set of new features. SCONE and sconify_image now support both musl as well as glibc-based binaries. We added a new network shield to support confidential service meshes.
SCONE Confidential PySpark on Azure Marketplace (2021-12-09)
We added new SCONE VM images on the Azure Marketplace. You can take confidential PySpark for a test drive by starting a VM on Azure. Moreover, you can experiment with some new SCONE features using the SCONE Playground.
SCONE Confidential Computing University (2021-11-24)
We added new videos as part of our Confidential Computing Course. We introduce confidential computing, confidential cloud-native applications, and confidential service meshes. We also introduce some interesting application domains: multi-stakeholder applications and confidential multi-parties learning. All videos include screencasts of demos that use SCONE to implement these concepts. We also added a new LADC keynote that addresses the use of confidential computing in critical applications.
SCONE Runtime Authentication (2021-10-23)
Often, we need to prevent adversaries from even being able to start a confidential application. For example, an adversary might otherwise be able to sign some documents. We added support for runtime authentication via OTPs (One Time Passwords). To show how to use this new feature, we added a simple OTP demo. This also shows how to mix secure command line arguments with user-provided arguments.
Confidential Multi-Stakeholder Workflows (2021-07-24)
SCONE supports sconified container images to become part of confidential multi-stakeholder workflows. We have just added one of our amazing animations to explain our approach.
Check out our Confidential Boutique Demo (2021-07-24)
We show how to sconify Google's Boutique Microservices demo. The microservices are written in a variety of programming languages and we show how to transform each of these in a single step into confidential service and run the applications on Azure.
1-Step transformation of a native into a confidential service (2021-06-21)
SCONE supports a single-step sconification of the container image of a native service into a confidential service: data and code are protected in Use, in Transit, and at Rest. SCONE attests each service and provisions it with secrets. We added a simple example. For a detailed description of features, read sconify_image.
We added some advanced confidential compute use cases (2020-03-20)
We explain how one can use the SCONE confidential computing platform to implement some advanced use cases. We show how to build confidential cloud-native applications (see Confidential Document Management), how to implement confidential federated machine learning, and how to establish trust with the help of a shared codebase using a SCONE confidential deployment.
We improved the integration with Azure services (2021-03-19)
SCONE supports MAA (Microsoft Attestation Service) in addition to Intel DCAP/EPID attestation: select as part of the attestation policy. Our policies can also retrieve secrets from AKV (Azure Key Vault) and securely distribute these to attested applications. In addition to a Flask-based Python application, we added a tutorial to show how to use MAA and AKV in the context of confidential AKS
SCONE Version 5.4 released (2021-03-12)
We released a new minor version which includes a sequence of bug fixes and new features like binary_fs, new CAS features (audit log), and updated sconeapps.
New episode of SCONE Confidential Computing Telenovela released (2021-02-23)
Meet our lovely protagonists Alice and Bob who have been working from their home office. They need to protect their teleconferences against Mallory - who has started to work as a cloud admin.
Confidential document management (2021-02-04)
We added a new confidential document management service that includes nginx as a proxy, a REST API written in Python, memcached as rate-limiter, and MariaDB as a database. All services
run inside of enclaves. All communication is encrypted. All code - including the Python code - is protected and attested. All services implicitly attest each other. One can deploy this with helm on Azure Kubernetes Services (AKS) or any Kubernetes cluster with access to Intel SGX.
Improved support for Azure (2021-02-01)
We support the Azure SGX Plugin in our helm charts. You can now just specify --useSGXDevPlugin=azure to use the SGX Plugin and
--set sgxEpcMem=16 (in MiB) to specify the required EPC size. We also added/updated helm charts for mariadb, maxscale, memcached, nginx, openvino, pytorch, spark, teemon, tensorflow, TensorFlowLite, and Zookeeper.
CAS Namespace Support (2021-01-03)
The newest version of SCONE CAS supports namespaces.
Operating Confidential Applications (2020-12-12)
We describe in the new operations section how to detect known security vulnerabilities and how to mitigate these.
Enhanced SCONE Policy Language released (2020-08-12)
The new version provides more control over the information in the generated certificates. Moreover, secrets can now be exported/imported to/from sessions located on another CAS instance (this is part of release 4.2).
Visual Studio Code and C# Support added (2020-06-13)
We combined Visual Studio Code with our SCONE cross-compiler. . For mono the program execution, as well as the compilation itself, runs inside of an enclave. See a simple C# hello world example.
Kubernetes Support added (2020-06-01)
SCONE supports deploying confidential applications to Kubernetes. We explain the basic concepts and we describe how to deploy confidential applications with helm like MariaDB. See also our deep-dive tutorial to show how to build and run an encrypted Python program in a Kubernetes deployment and to use some new features such as policy-based certificate generation and injection.
Getting Started
To get started with the SCONE Confidential Compute Platform, we recommend to
-
read on how to sconify an application / a service in a single step into a confidential application / service, i.e.:
- data and code are protected in Use, i.e., a service runs inside of a trusted execution environment,
- data and code are protected at Rest, i.e., files are transparently encrypted/decrypted, and
- data and code are protected in Transit, i.e., while being transferred between TEEs.
- secrets are always protected and policy-defined key release, i.e., a service is automatically attested and provisioned with secrets,
Note that SCONE-based services can be executed on-premise or in a cloud-like AKS. The SCONE-based services are typically contain-based but they can also run as binaries inside of a VM or directly on a host machine. SCONE-based services do not have any network connection to Scontain. They can even be executed in air-gapped settings. If one uses an air-gapped system, one needs, however, to be care on how to setup up attestation.
Prerequisites
- register a free account at our container registry,
- ask to get access to
sconify_imageby sending an email to info@scontain.com, - try out a sconify_image example.
SCONE - in a nutshell
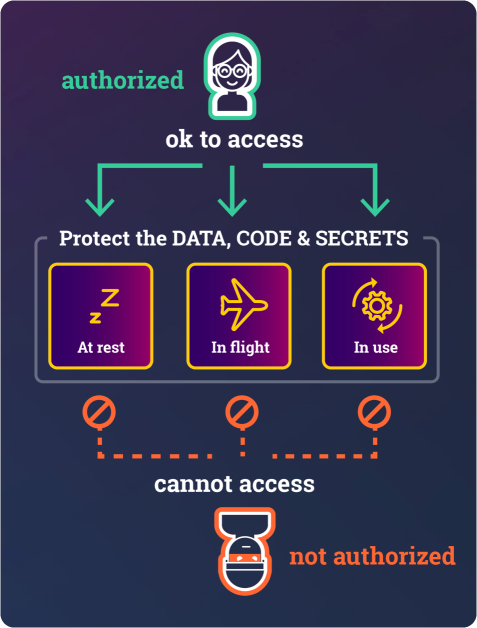
- an application's data, secrets, and code
everywhere, i.e.,
- in main memory - at runtime,
- on disk - at rest, and
- on the network - during communication
and during the entire lifetime of the application by addressing vulnerabilities by supporting
- software updates of the application, and
- firmware and hardware updates.
while reducing the cost and effort
- of migrating to SGX with the help of a lift and shift approach, and
- of operating SGX-based applications by permitting to outsource most of the maintenance to cloud providers
ensuring excellent security by supporting
- a security policy to store, generate, share secrets (e.g., key pairs and certificates) and inject these into applications, and
- a defense-in-depth approach to protect also against known and unknown vulnerabilities
and supporting
- classical applications running on bare metal servers,
- modern cloud-native applications running in containers and VMs,
- integration in CI/CD pipelines,
- deployment with
helmon Kubernetes, - ensuring state-of-the-art availability with the help of Kubernetes, and
- using managed Kubernetes services.
SCONE Executive Summary
The SCONE confidential computing platform facilitates always encrypted execution: one can run services and applications such that neither the data nor the code is ever accessible as plain text - not even for root users. Only the application code itself can access the unencrypted data and code. SCONE simplifies encrypting the input, executing the service/application in encrypted memory on an untrusted host, transparently encrypting the output, and shipping the output back to the client.
SCONE (Secure CONtainer Environment) supports the execution of confidential applications inside containers running inside a Kubernetes cluster (basic concepts). SCONE also supports the execution of confidential applications inside of VMs (e.g., on top of Windows10) as well as directly on a host (baremetal). SCONE supports all common programming languages. It also supports air-gapped systems both with SGXv1 as well as SGXv2.
The memory size of SCONE-based applications can be up to 32GB on current SGX-capable CPUs. The SGX specification updates published by Intel show that upcoming CPUs will support even larger enclaves, and SCONE will - on these CPUs - support applications with basically unlimited memory sizes.
SCONE supports the execution of existing programs inside of enclaves (at use encryption): this includes both programs linked with glibc (default for Ubuntu, Centos, RHEL) as well as musl (default on Alpine Linux and hence, many container images). SCONE supports all popular programming languages and supports static and dynamic linking. For the development of applications, we support a cross-compiler, which is our recommended way to develop confidential applications.

SCONE helps to ensure that data, communications, code, and the main memory are always encrypted. To do so, SCONE needs to verify (i.e., attest) that the expected application code is running in a trusted execution environment on a potentially untrusted host. Read our secure remote execution tutorial to see how to perform an encrypted remote execution in a single step. In this way, one can even execute encrypted code. We show how to execute encrypted Python scripts in the context of blender, an encrypted word count and a hello world program.

SCONE can help you to encrypt your input and output data on your local computer. The keys are managed with the help of SCONE CAS (Configuration and Attestation Service). SCONE CAS itself runs, of course, inside an enclave. It can either run on the client-side or on a remote host. It can even be operated by an untrusted entity and still be trusted by CAS clients.

SCONE supports multiple stakeholders (confidential multiparty computation) that do not necessarily trust each other. SCONE supports users, service providers, application providers, data providers, and infrastructure providers. They can all work together, and SCONE can ensure that each party can protect its own intellectual property. Some of the services, like SCONE CAS, can be operated by not necessarily trusted stakeholders since clients can verify that the services are in the correct state.
If you are interested in confidential multi-party computations, we can give you access to a proof of concept that shows how to protect AI models and provide access control to the model, e.g., can only be executed on certain machines, and only certain arguments can be provided by the user - depending on a given SCONE policy. Just send us an email.
